If you’re preparing for a networking, Linux system administration, DevOps, or cybersecurity interview, understanding network ports is a must. Port numbers come up in almost every technical interview because they’re essential for network communication. Yet, many candidates overlook this basic area.
This article covers the top 25 ports you should know by heart, including what each one does, the protocol behind it, and why it matters. Whether you’re a beginner or just need a refresher, this guide is crafted to be simple, practical, and interview-ready.
What Are Network Ports?
Before we get into the list, let’s get a quick grip on what a port really is.
In the networking world, a port is not a physical thing — it’s a virtual channel that allows communication between computers. Think of it like a room number in a hotel. Your IP address is the hotel address, and the port tells the computer which service (room) you’re trying to access.
Each port is assigned a number between 0 and 65535:
Why Do Interviewers Ask About Ports?
Because it tests your understanding of:
- Which services run on which ports
- The difference between TCP and UDP
- How to troubleshoot connectivity issues
- Security implications of open ports
You’ll often hear questions like:
- What port does SSH use?
- How do you check for open ports in Linux?
- Can you explain the difference between ports 80 and 443?
The Top 25 Ports You Must Know (With Descriptions)
Let’s go over the most common ports you’ll see in interviews and when working with real systems.
| Port | Protocol | Service Name | Purpose |
|---|---|---|---|
| 20 | TCP | FTP (Data) | Transfers file data (active mode) |
| 21 | TCP | FTP (Control) | Command/control for FTP transfers |
| 22 | TCP | SSH | Secure remote login/file transfer |
| 23 | TCP | Telnet | Remote login (insecure, legacy) |
| 25 | TCP | SMTP | Sending emails |
| 53 | TCP/UDP | DNS | Resolving domain names to IPs |
| 67 | UDP | DHCP Server | Assigns IP addresses |
| 68 | UDP | DHCP Client | Receives DHCP configuration |
| 80 | TCP | HTTP | Standard (insecure) web traffic |
| 110 | TCP | POP3 | Older email retrieval protocol |
| 123 | UDP | NTP | Syncing system time |
| 135 | TCP | RPC | Windows services communication |
| 137 | UDP | NetBIOS Name Service | Windows name lookups |
| 138 | UDP | NetBIOS Datagram Service | Windows browsing |
| 139 | TCP | NetBIOS Session Service | File/printer sharing in older Windows |
| 143 | TCP | IMAP | Email retrieval (modern) |
| 161 | UDP | SNMP | Monitoring routers, switches, etc. |
| 389 | TCP/UDP | LDAP | Centralized authentication (like Active Directory) |
| 443 | TCP | HTTPS | Secure web traffic |
| 445 | TCP | SMB over TCP | Modern Windows file sharing |
| 465 | TCP | SMTPS | Secure SMTP (legacy) |
| 514 | UDP | Syslog | Centralized logging |
| 993 | TCP | IMAPS | Secure IMAP |
| 995 | TCP | POP3S | Secure POP3 |
| 3306 | TCP | MySQL | Popular database service |
| 5432 | TCP | PostgreSQL | Open-source SQL database |
| 5900 | TCP | VNC | Remote desktop access (GUI) |
| 6379 | TCP | Redis | In-memory key-value store |
| 8080 | TCP | HTTP Alternate | App servers, proxies |
| 8443 | TCP | HTTPS Alternate | Secure access to custom web apps |
Quick Tip: Just remember these four ports: 20/21 for FTP, 22 for SSH, 80 for HTTP, and 443 for HTTPS – these are the most important ones to know.
Port Categories to Make Life Easier
Instead of memorizing all ports randomly, group them:
| Category | Port(s) | Service Name |
|---|---|---|
| Remote Access | 22 | SSH (Secure Shell) |
| 23 | Telnet | |
| 5900 | VNC (Virtual Network Computing) | |
| Email Services | 25 | SMTP (Simple Mail Transfer Protocol) |
| 110 | POP3 (Post Office Protocol) | |
| 143 | IMAP (Internet Message Access Protocol) | |
| 465, 993, 995 | SMTPS, IMAPS, POP3S (Secure versions) | |
| Web Services | 80 | HTTP (HyperText Transfer Protocol) |
| 443 | HTTPS (HyperText Transfer Protocol Secure) | |
| 8080, 8443 | Alternate HTTP/HTTPS (for web apps or proxies) | |
| File Sharing & Transfers | 20/21 | FTP (File Transfer Protocol) |
| 139/445 | SMB (Server Message Block) | |
| 3306/5432 | MySQL/PostgreSQL (Databases) | |
| Name and Address Services | 53 | DNS (Domain Name System) |
| 67/68 | DHCP (Dynamic Host Configuration Protocol) | |
| 123 | NTP (Network Time Protocol) | |
| 137–139 | NetBIOS (Network Basic Input/Output System) | |
| Monitoring and Logging | 514 | Syslog (System Logging) |
| 161 | SNMP (Simple Network Management Protocol) |
How to Check Open Ports on a Linux System
Let’s take a closer look at how to check open ports on a Linux system using a command such as ss, netstat, and nmap.
1. Using ss (Modern and Fast)
The ss command (short for socket statistics) is a modern replacement for the older netstat command. It’s designed to be faster and more efficient for listing open ports and network connections.
sudo netstat -tulpn
Explanation of the command:
-t: Shows TCP sockets.-u: Shows UDP sockets.-l: Displays only listening sockets (ports that are open and waiting for incoming connections).-p: Shows the process that owns the socket (i.e., which application is using the port).-n: Displays port numbers in numeric form (avoiding the need to resolve them to service names).
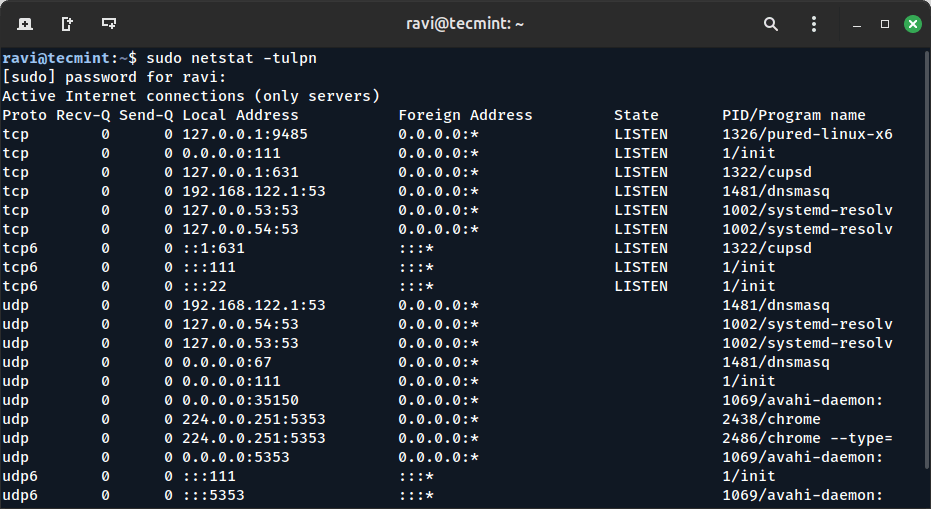
2. Using netstat (Older but Still Common)
The netstat is a legacy command that was widely used before ss gained popularity. It still exists on most Linux distributions and can be useful in situations where ss might not be available, or when you are working with older systems.
sudo netstat -tulpn
Explanation of the command:
-t: Displays TCP sockets.-u: Displays UDP sockets.-l: Shows only listening ports (no established connections).-p: Shows the process ID (PID) and the name of the program using the socket.-n: Outputs numerical addresses and ports (instead of resolving them to service names like “http“).
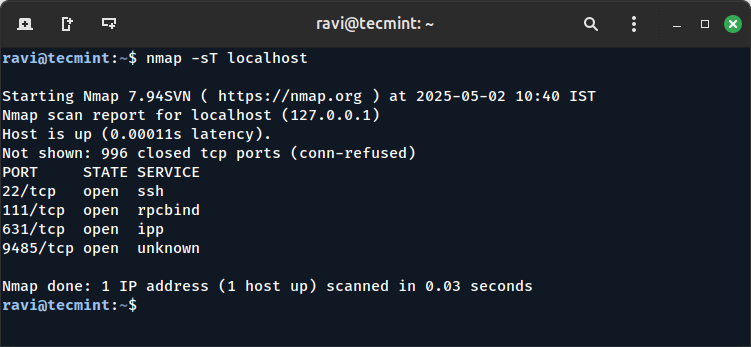
3. Scanning with nmap
The nmap (Network Mapper) is a powerful tool primarily used for network exploration and security auditing. It can be used to scan your own system or any remote system to find open ports.
Unlike ss and netstat, nmap is usually used for more detailed network scanning and can provide information about external systems as well.
nmap -sT localhost
Explanation of the command:
-sT: It tries to make a full connection to each port and checks which ones respond.localhost: Refers to the local machine you want to scan. You can replace localhost with any IP address to scan remote systems.
Security Tip: Why Knowing Ports Helps You Stay Safe
Attackers often use port scanning techniques to identify open ports and find services that may be vulnerable. Understanding which ports are exposed on your system is essential for maintaining security.
Here are a few examples of risks associated with commonly open ports:
- Port 23 (Telnet): If this port is open, your system could be vulnerable to attacks, as Telnet transmits data, including passwords, in plain text.
- Port 445 (SMB): This port is often targeted by ransomware and other malware, and leaving it open can give attackers access to sensitive files and resources across your network.
As a Linux or DevOps engineer, it’s your responsibility to proactively secure your system. Here are key strategies to mitigate risks:
- Close Unused Ports: Keep only the necessary ports open. If a service isn’t being used, it’s safer to close that port.
- Use Firewalls: Configure firewalls like ufw (Uncomplicated Firewall) or firewalld to restrict which ports can be accessed, ensuring that only authorized traffic reaches your system.
- Secure Exposed Services with Encryption: For services that need to be accessible, such as SSH or HTTPS, always enforce encryption to protect data in transit from potential eavesdropping.
To block traffic on port 23 (Telnet), use ufw:
sudo ufw deny 23
To deny traffic on port 23 (Telnet), use firewalld:
sudo firewall-cmd --zone=public --add-port=23/tcp --permanent --remove-port=23/tcp
By understanding ports and properly securing them, you minimize the attack surface of your systems, enhancing both their security and performance.
Final Thoughts
Understanding port numbers isn’t just about memorizing them, it’s about knowing how services communicate in Linux and on networks. Once you understand the basics, you’ll be better at troubleshooting, securing your systems, and passing technical interviews.